GitHub Enterprise Server 3.10 is now generally available. With this version, organizations are able to give developers and administrators more control over their repositories with enhanced security and compliance controls, and ensure secure development is a top priority.
Highlights of this release include:
- GitHub Projects is generally availablewith additions that help teams manage large projects (#650)
- Always deploy safelywith custom deployment protection rules for GitHub Actions (#199) and new policy control over runners
- Start finding vulnerabilities in all your repositories, in just a few clicks with a new default setup experience for GitHub Advanced Security code scanning (#642), and track security coverage and risk at the enterprise level (#766)
- Fine-grained personal access tokens (PATs) bring granular control to PATs (#184)
- Branch protections meet more compliance needs with more control over merge policies
- Backup instances faster and more incrementally, for more confident operations
Download GitHub Enterprise Server 3.10 now.
For help upgrading, use the Upgrade Assistant to find the upgrade path from your current version of GHES to this new version.
GitHub Projects is generally available
Organize and track your team’s work directly on GitHub using the new Projects, now generally available on Enterprise Server.
Built like a spreadsheet, project tables give you a live workspace to filter, sort, and group issues and pull requests. This gives administrators greater visibility across everything that’s happening, and development teams can collaborate and stay in flow more efficiently.
Before GitHub Projects, I would have needed two or more tools to get context from interdisciplinary teams on their projects. Now I can get context at a glance all in one place, so teams can be efficient and stay in the flow.
Always deploy safely, with custom deployment protection rules for GitHub Actions
Shipping software faster means knowing you’re doing so safely. That means deployments need to be both governed and automated. Teams using GitHub Actions for continuous deployment have long been able to protect specific environments to enforce deployment protection rules, such as requiring approval from specific team members.
With GitHub Enterprise Server 3.10, teams can create their own custom deployment protection rules (beta) to set up rigorous guardrails that ensure only the deployments that pass all quality, security, and manual approval requirements make it to production.
What’s more, this release also gives administrators new control over the security and management of runners for GitHub Actions. Centrally managing self-hosted runners is a best practice that helps companies ensure that runners aren’t compromised by untrusted code in a workflow. Now, enterprise administrators can disable repository level self-hosted runners across organizations and user namespaces, ensuring that all jobs are hosted on centrally governed machines.
Start finding vulnerabilities in all your repositories, in just a few clicks
We’re always looking for ways to make it easier for developers to secure their code. This means building security tools that provide a frictionless experience for developers so they can focus on innovation. With code scanning, automated security checks are run with every pull request, surfacing issues in the context of the development workflow and empowering developers to fix 48% of vulnerabilities in real time and 72% within 28 days.
In this release, we’re making it easier for all developers to realize these results with seamless enablement. Developers can now set up code scanning on a repository in just a couple of clicks – without using a .yaml file – with the new “default setup”. What’s more, teams can also enable code scanning across multiple repositories at once with default setup.
So in minutes, you can start finding and fixing vulnerabilities across thousands of repositories in your enterprise. Security, at speed–check!
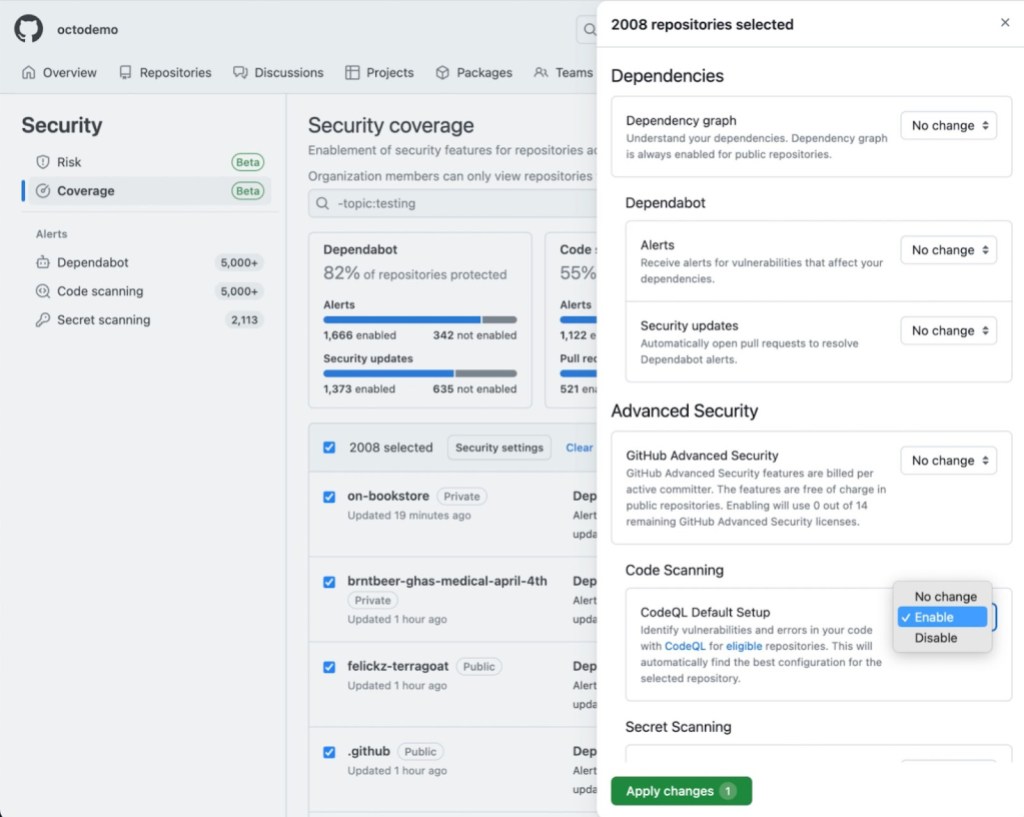
Track security coverage and risk across your enterprise
With Dependabot, code scanning and secret scanning enabled across your enterprise, it’s now easier for central security teams to track coverage and risk across all your repositories–with risk and coverage insights now included in the enterprise-level “code security” pages. Drill down by Team or Organization to drive directed roll out and remediation programs.
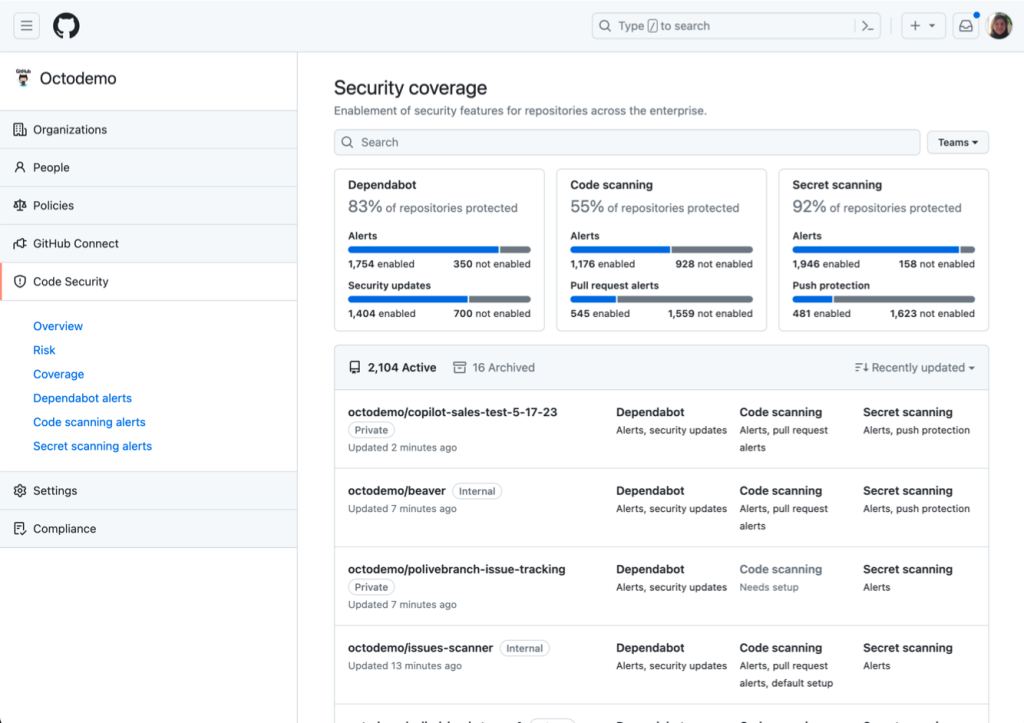
It’s also now easier for teams to prioritize their own remediation efforts, with tools such as the ability to filter alerts on a repository by file path or language.
Oh–and we’re also pleased to announce Swift support for code scanning. This launch, paired with our launch of Kotlin support in Enterprise Server 3.9, means that CodeQL, the engine that powers GitHub code scanning, covers both iOS and Android development languages. Note that Swift is not yet supported as a default setup language, and this will be added in a later release.
Minimize risk with fine-grained Personal Access Tokens
Classic PATs can be granted broad permissions across all repositories a user has access to. As a result, if one is leaked, the risk can be significant.
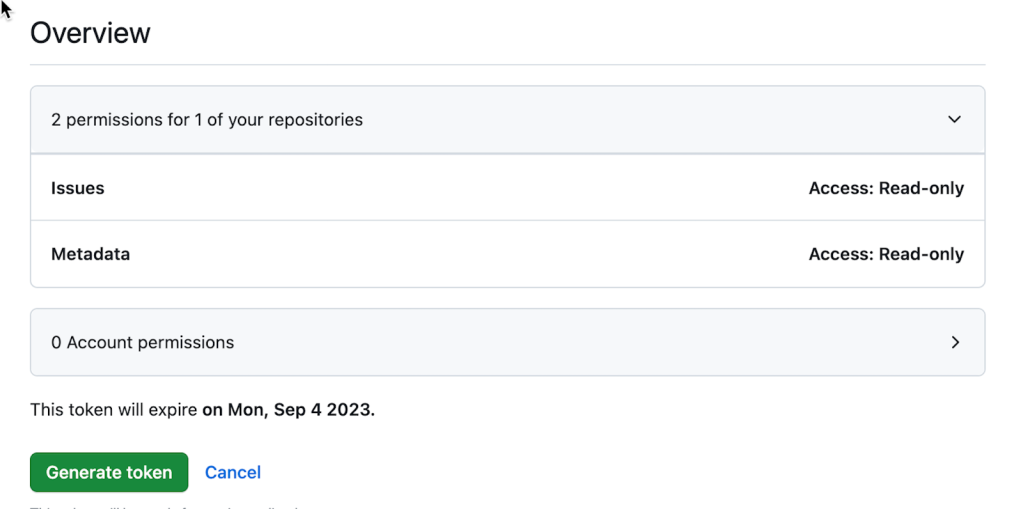
Fine-grained PATs minimize this risk. They allow developers to grant a PAT permissions from a set of over 50 granular permissions. Each permission can be granted with either ‘no access’, ‘read’, or ‘read and write’ access. Fine-grained PATs also have an expiration date, and they only have access to the repositories or organizations they are explicitly granted access to. This makes it easy for developers to follow a least privileged access model when using PATs.
Branch protections meet more compliance needs
Branch protection rules give you a lot of control over how to enforce approval processes for compliance. In this release, we’ve refined this control with two key updates: changes to how required approvals are enforced, and allowing you to prevent the last pusher from approving a pull request. For more details on how required approvals are now enforced, read our recent blog post.
Backup instances faster
Regular backups and upgrades are a core part of managing Enterprise Server instances. This release includes enhancements across these operations, from updating ghe-migrations to show the status of all database migrations during an upgrade, to incremental mySQL backups, and the ability to prune backup snapshots in backup-utils v3.10.0 outside of the backup generation process so backups can be taken more quickly.
Try it out today
To learn more about GitHub Enterprise Server 3.10, read the release notes or download it now.
Not using GHES already? Start a free trial to innovate faster with the developer experience platform companies know and love.







