Update 06/26/24 at 12:50 p.m.:
The hacker and developers collective Rabbitude told Gizmodo that Rabbit finally revoked the original ElevenLabs API key, allowing them access to users’ AI responses and the device’s voice model. However, there’s a new twist. The group now claims it also had access to Rabbit’s internal messaging service.
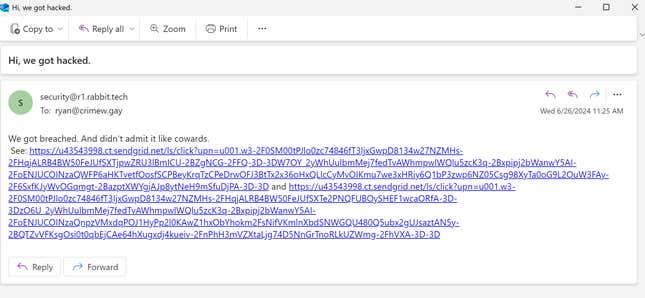
In a Wednesday post to the group’s site, Rabbitude said that the Rabbit R1 makers canceled all the previously revealed API keys; one was so poorly done it bricked users’ devices for a short while until it could re-reinstate ElevenLabs. However, the group wasn’t ready to take Rabbit off the hook and shared it had yet another API key that was hardcoded into the Rabbit. This one was for Sendgrid, the email service used for the r1.rabbit.tech subdomain. The hacker group says the domain houses spreadsheets containing sensitive user data.
To share proof of the breach, one of the group’s developers shared an email with Gizmodo sent from the security@r1.rabbit.tech address. The group says it sent a similar email as a test more than a month ago, but that went unnoticed by Rabbit’s developers.
As further proof, the group sent more emails from the rabbit@r1.rabbit.tech address to Jason Koebler at 404 Media. That email was previously used to share press announcement details with journalists.
Rabbit did not immediately return a request for comment. We’ll be looking out to see if the developers have anything more to share about the growing breach. Our point still stands: if you were using a Rabbit R1, you should put that on pause until Rabbit shares any concrete details about its internal security.
Original Story:
That $200, blazing orange, minimalist AI doohickey called the Rabbit R1 promised it would become your go-to AI companion. Instead, it proved it was a malformed and half-baked machine that couldn’t match up to any of its lofty promises. Now, according to a group of white hat hackers, it’s even worse than that. The team calling themselves Rabbitude claims they’ve had access to all the Rabbit R1’s codebase API keys for over a month, granting them a peak at all of Rabbit’s responses, including any sensitive information offered to the AI.
All this is to say, if you’re still one of those little hares who still jump at the chance to use a Rabbit R1, you should stop doing so immediately.
Rabbitude claimed it gained access to the Rabbit codebase back on May 16. The team also shared the API keys that allow the Rabbit to connect to Google Maps and Yelp, which gives the AI models access to local reviews and directions. The team also says it has access to the ElevenLabs keywhich is the system Rabbit uses for text-to-speech. That last one is particularly important to everyday Rabbit operations since it lets the hackers get a history of all past text-to-speech messages and even brick the device by deleting the voices entirely.
After the hacker group released its findings late Tuesday, one of the members who goes by Eva online said ElevenLabs temporarily revoked the ElevenLabs API key, which also shut down all Rabbit devices for a time before it went back online. They said, “Rabbit knew about it and did nothing to fix it.”
Gizmodo contacted Rabbit early Wednesday morning for a comment, but we did not immediately hear back. The company told Engadget that it was aware of the alleged breach but was “not aware of any customer data being leaked or any compromise to our systems.” Gizmodo also asked Rabbit if it has revoked any API keys, though we’ll update this post if we hear more.
The Rabbit R1 is already prone to failure since it relies so much on cloud services that are not directly controlled by the Rabbit team. Last month, a ChatGPT outage temporarily made the device utterly useless. Gizmodo could not independently confirm whether the Rabbit went offline due to any meddling with the ElevenLabs API. We contacted the hacker team for proof and comment, and we’ll update this story if we hear more.
Tech blogger Ed Zitron has already detailed the company’s transformation from working on a crypto metaverse project to its AI device. YouTuber CoffeeZilla also broke down some of the more concerning aspects of the device, including some “serious data privacy concerns” after looking at the Rabbit’s codebase. He mentioned “things malicious actors could use to get access to all the replies the R1 has ever given.”
On the Rabbitude Discord, the team claims they have been working with CoffeeZilla since they accessed that codebase over a month ago. The team further said, “This is real. Rabbit can dance around it all they like, but it is real, and this did happen. They had a month to change the keys, and they didn’t. That’s on them.”






