A major privacy concern involving more than 40,000 security cameras worldwide has been revealed by Cybersecurity firm Bitsight. According to the company’s TRACE research division, these cameras are live-streaming video feeds that are fully exposed to the internet — meaning that one can gain access without needing any sort of authentication, encryption, or even a basic password. In most cases, a person can access real-time footage from these exposed cameras simply by knowing their IP address.
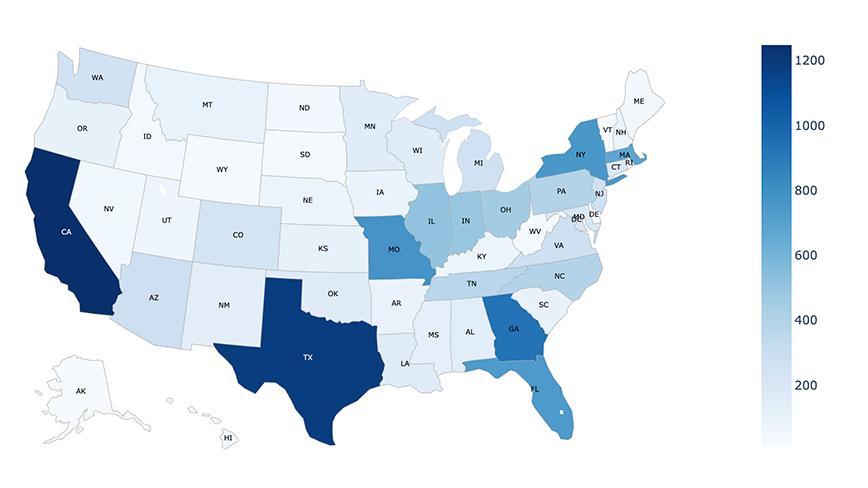
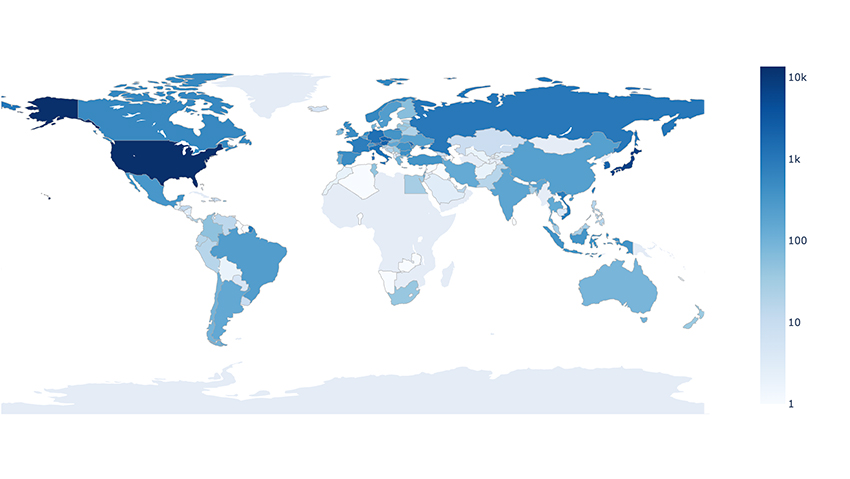
Bitsight initially flagged the issue back in 2023, but recent research suggests that the situation “hasn’t gotten any better.” According to the latest research, these vulnerable cameras are not limited to one region or industry. The United States has close to 14,000 cameras that are potentially exposed, with states like California, Texas, Georgia, and New York having the highest numbers. Next on the list is Japan, with 7,000 exposed cameras, followed by Austria, Czechia, and South Korea, each of which have close to 2,000 vulnerable devices.
It is true that not every camera hooked up to the internet is a cause for concern, and some livestreams are set up intentionally to showcase scenes, like a beach or a birdhouse, for public viewing. However, some of these vulnerable cameras have been found in more private environments — including residential setups monitoring front doors, backyards, and even living rooms.
Cameras in office spaces, factories, as well as public transportation systems were also found. Bitsight researchers were able to observe sensitive spaces, monitor foot traffic, and, in some cases, even see details written on whiteboards — all in real time. The majority of the exposed devices are said to be using HTTP, while the rest stream through RTSP (Real-Time Streaming Protocol), which is a common protocol for controlling and managing streaming media over IP networks.
In addition to raising privacy and surveillance concerns, these exposed devices pose serious security risks. Information collected by Bitsight’s Cyber Threat Intelligence team suggests that users are openly discussing the feeds on dark web forums, where users are sharing tools and techniques to gain unauthorized access, and even selling access, to unprotected video streams.
Users and organizations are advised to double-check on how their cameras are configured: Disable remote access if not in use, update to the latest firmware, and make sure the device is protected behind a firewall or connected to a secure network. A simple way to check whether your camera is exposed or not is by accessing it from outside your home network. If you are able to view the camera feed without logging into a secure app or using a VPN (Virtual Private Network), it’s likely open to anyone on the internet. Additionally, one should replace any default usernames and passwords as many camera devices ship with a default set of credentials that are easy to crack.
Follow Tom’s Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.