A zero-day vulnerability (CVE-2025-21042) in Samsung’s Android image processing library allowed attackers to embed spyware called LANDFALL in Samsung devices including Galaxy handsets. Here are some definitions; a zero-day vulnerability is one that no one knows about giving the developer zero days to come up with a way to patch the flaw. Samsung’s Android image processing library handles the decoding and processing of various image formats, including some formats that are proprietary to Samsung.
The LANDFALL spyware impacted certain Samsung phones
LANDFALL hasn’t been a threat since this past April although another zero-day vulnerability was patched by Samsung just two months ago during September. This flaw (CVE-2025-21043) was also found in the imaging processing library. The patch prevents any attack from taking place.
The spyware used microphone recording, location tracking, and photos for surveillance
Itay Cohen, a senior principal researcher at Palo Alto Network’s Unit 42 said that the LANDFALL attack was targeted at certain individuals and was not mass-distributed. Cohen says that the motive for these attacks was espionage.
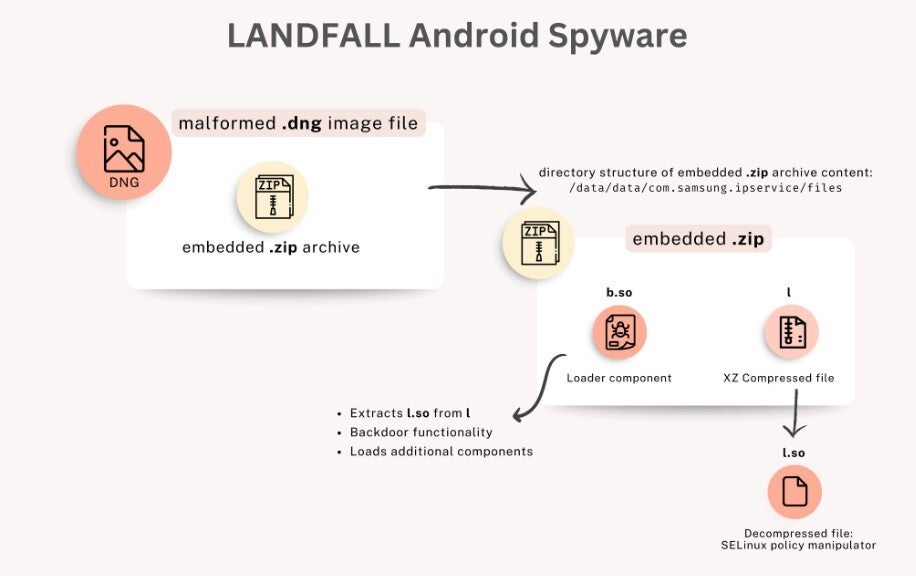

Flowchart for the LANDFALL spyware. | Image credit-Techworm
We should point out that the LANDFALL spyware was designed for attacks against the Samsung Galaxy line mostly with targeted attacks taking place primarily in the Middle East including Turkey, Iran, Iraq, and Morocco. Being spyware, it shouldn’t be a surprise that LANDFALL used microphone recording, location tracking, photos, contacts. A malformed image file, one that has been deliberately corrupted to set off a flaw in the software that reads the file, was used in the attacks. No clicks were required to exploit the vulnerability.
- Record microphone audio and phone calls.
- In real time, track GPS location.
- Access photos, messages, contacts, call logs, and browsing history.
- Hide from antivirus scans and even remain active after reboots.
For 10 months targeted phones were extremely vulnerable
There was a period of 10 months between the time the campaign began in July 2024 and when the flaw was patched in April of this year when the aforementioned Galaxy models were at the peak of their vulnerability. When Samsung patched the vulnerability this past April, the company made no public statement about it.